Breadth of Integration
Identity and Access Management Solution
Secure Access For Your Business Applications
Managing complex passwords and security protocols is overwhelming. CENTAGATE® provides a simple solution to safeguards your application from unknown users.
Free Consultation
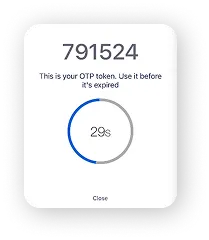
Take Your Workforce and Users From Reused Passwords to Passwordless
Centagate evolve your access security with smarter, stronger authentication.
Bad
Password Only
1234
Qwerty
Password
iloveyou
Qwerty
Password
iloveyou
Good
Password +
SMS
Voice
Voice
Good
Password +
Authenticator
Software Token OTP
Hardward Token OTP
Software Token OTP
Hardward Token OTP
Best
Passwordless
Windows Hello
Anthenticator (Phone Sign-in)
FIDO2 Security Key
Anthenticator (Phone Sign-in)
FIDO2 Security Key
A Smarter Way to Authenticate Every Login and Access
Here’s how CENTAGATE® secures your Login box and access
Step 1
Spot the Danger
Most people still reuse the same password everywhere — or write it on a sticky note. That’s how attackers get in. One weak login can open the door to your entire system.
Step 1
Spot the Danger
Most people still reuse the same password everywhere — or write it on a sticky note. That’s how attackers get in. One weak login can open the door to your entire system.
Step 1
Spot the Danger
Most people still reuse the same password everywhere — or write it on a sticky note. That’s how attackers get in. One weak login can open the door to your entire system.
Stop Phishing at the Door
Traditional login methods rely on passwords — the weakest link in your security chain.
Centagate replaces password-based access with secure, phishing-resistant
authentication.

Password-Based Vulnerabilities
- Employees reuse weak passwords across systems.
- Employees click malicious links (even with training)
- SMS/email OTPs intercepted by attackers
- One click on a fake login page compromises your entire network.
Result: Blocks bots but not identity

Using CENTAGATE® (and Passwordless)
- Passwordless login using FIDO2 keys, biometrics, or mobile authentication.
- Nothing to type = nothing to phish
- FIDO2-certified hardware keys/biometrics
- Centralized security policies ensure compliance without user friction.
Result: Users are correctly authenticated and authorised to carry out the appropriate activities.
Benefits of Using CENTAGATE®
Secure Access Without Complicating Things
Protects your digital systems using secure login methods like:
- Biometrics (fingerprint or face)
- Mobile-based OTP
- Passwordless logins
Only the right people get in — no more risky password reuse.
Know Exactly Who Logged In
Unlike traditional login methods or CAPTCHAs, CENTAGATE®️ gives you:
- Verified identities (not just “someone with the right password”)
- Real-time tracking of login activity
You can trust the identity behind every action in your system.
Works with What You Already Have
CENTAGATE®️ integrates easily with:
- Existing apps (via SAML, OAuth, Restful API)
- VPNs and network tools (via RADIUS)
- Cloud systems (Google Workspace, Microsoft 365, etc.)
No need to replace your current systems — CENTAGATE®️ fits right in.

CENTAGATE® in Action: Tailored for Every User
Make your identity and access management simple, secure, and scalable — whether you're protecting your team or your customers.

Workforce Identity
Secure logins, simplified access, and complete control over who’s doing what.

Customer Identity
Ensure secure and seamless access, without introducing unnecessary friction.
CENTAGATE® has been recognised as a top choice for its value, functionality, and customer support.
Secure Systems Every Step of the Way
Centagate® safeguards your enterprise from user onboarding to transaction approval through strong authentication, centralised policies, and seamless integrations.
- Secure Identity Enrollment
- Mobile Provisioning
- MFA
- Active Directory
- Radius
- SAML
- Openlogin
- FIDO2
- RESTful API
- Risk Scoring
- Role-Based Policy
- Transaction-based Access
- Digital Signature
- MFA
- Mobile OTP
- SMS OTP
- QR Signature
- Mobile App Signing
Secure Identity for Every Industry

Finance & Banking

Corporate & Enterprise

Education

Technology

Healthcare
