Mobile App Push (Centagate Authenticator)
CENTAGATE® Features: Multifactor Authentication (MFA)
Secure Logins with Multiple Layers of Protection

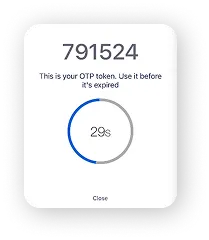
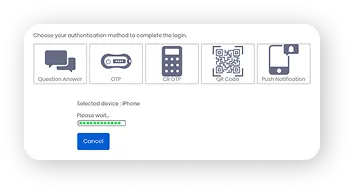



What is MFA?
Multi-Factor Authentication (MFA) adds an extra layer of security beyond just a username and password.
It verifies a user’s identity using two or more factors:
- Something you know (password)
- Something you have (mobile device, token)
- Something you are (fingerprint, face)
How CENTAGATE® Does It Better
CENTAGATE lets you choose and combine multiple authentication methods, depending on your users, risk level, and access policies.
Supported Authentication Factors:

Meet CENTAGATE® Your Identity Security Partner
Centagate Turnkey Solution is a ready-to-deploy identity and access management (IAM) platform that secures your environment without the typical hassle.
You get a full IAM setup — pre-configured, locally supported, and enterprise-ready — so you can protect access across web apps, VPNs, and cloud services quickly.
Here’s how it works
Assess & Align
Deploy & Integrate
Train & Support
Where You Can Use MFA?
CENTAGATE MFA works across:


Using CENTAGATE® (and Passwordless)
Key Benefits of Using MFA
Prevent Credential Theft
MFA makes stolen passwords useless without the second factor.
Flexible User Experience
Every user from Admin, Supervisor to Team have different views and workflow.
Centralised Policy Management
Define MFA rules from a single admin panel. No more siloed tools.
Easy Rollout
MFA can be enabled by group, user type, or integration — no need for rip-and-replace.
FAQs
1. What exactly is MFA—and why is it not just another annoying extra step?
It’s more than just another login hassle. Multifactor Authentication (MFA) means requiring two or more verification checks—like something you know (your password), something you have (your phone or hardware key), or something you are (a fingerprint). Centagate plays smart by letting you mix and match factors—mobile app push, TOTP, SMS/email OTP, FIDO2 keys, QR codes, even hardware tokens. So instead of juggling endless passwords or resorting to sticky notes, you add a solid second—or third—layer of defense, tailored to your risk level.
2. Can we integrate this without tearing down our current setup?
Absolutely. Centagate’s toolkit is turnkey—pre-configured, enterprise-ready, and deployable on your terms (on-prem or cloud). It slides right in via SAML, OAuth, SDKs, API, RADIUS, LDAP/AD—you name it. Roll-out MFA by user group, risk profile, or app, without causing chaos or replacing everything.
3. Will MFA make logging in a pain for our team—or our customers?
Not the way Centagate does it. They let you tailor the experience by role—admins, supervisors, or general users each see what’s relevant to them. Plus, MFA triggers can be context-aware: every login, high-risk transactions, unfamiliar devices or locations—you’re in the driver’s seat on friction vs. security.
4. What’s the point if someone just steals our password anyway?
Exactly. A compromised password, by itself, is basically worthless against MFA—so even if it’s compromised, access is still gated by that second factor. That means one data breach doesn’t necessarily become a system-wide collapse. With centralized policy control, you manage this from one admin panel—streamlining security instead of complicating it.